Exploring the Depths of Online Privacy: Tor Browser Unveiled
In an era where digital footprints are as ubiquitous as the air we breathe, safeguarding our online privacy has become an imperative. With cyber threats looming large and concerns about data breaches escalating, internet users are seeking refuge in tools that offer a shield against prying eyes. One such formidable guardian of online anonymity is the Tor Browser.
Unraveling the Enigma: What is Tor Browser?
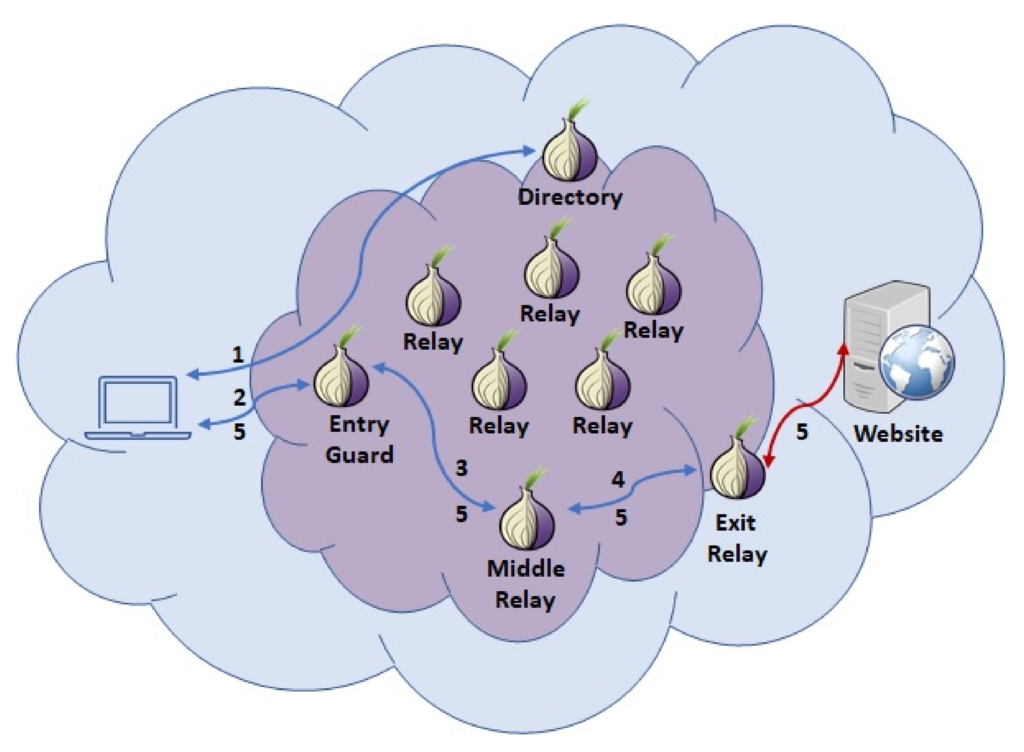
Tor, short for “The Onion Router,” is a free and open-source web browser that grants users access to the internet through a network of volunteer-operated servers. The name “Onion Router” derives from its method of data encryption, which involves layering multiple encryption protocols like the layers of an onion.
The essence of Tor lies in its ability to anonymize online traffic by bouncing it through a series of these volunteer-operated servers, or nodes, before reaching its final destination. This intricate process effectively conceals the user’s IP address and encrypts their connection, making it exceedingly challenging for any entity to trace their online activities.
The Pillars of Tor Browser’s Strength
1. Anonymity and Privacy:
- Tor Browser is a stalwart defender of online privacy, allowing users to surf the web without revealing their true identity. This is particularly crucial for individuals in regions with restricted internet access or oppressive regimes.
2. Circumventing Censorship:
- In regions where internet censorship is prevalent, Tor Browser serves as a lifeline. By routing traffic through a network of relays, it evades most forms of censorship, enabling users to access information that may otherwise be blocked.
3. Security at its Core:
- Tor Browser is fortified with multiple layers of encryption, rendering it an immensely secure tool for online activities. It provides an added layer of protection against eavesdropping and man-in-the-middle attacks.
4. No Tracking, No Ads:
- Unlike mainstream browsers, Tor Browser doesn’t engage in user tracking or profiling. This means no targeted ads and no surreptitious data collection.
5. Empowering Free Speech:
- Tor Browser is a bastion for free speech advocates, journalists, and whistleblowers. It provides a platform where individuals can voice their opinions and expose truths without fear of retribution.
Navigating the Tor Ecosystem
The Tor ecosystem extends beyond the browser. It includes the Tor network itself, which is a decentralized network of volunteer-operated servers, and other applications like the Tor Relay and Tor Messenger. This vast ecosystem works in tandem to fortify online privacy and security.
Is Tor Browser Right for You?
While Tor Browser is a formidable tool for privacy-conscious individuals, it’s essential to recognize that it may not be the optimal choice for every online activity. Due to its layered encryption process, it can be slower than conventional browsers, which may not be ideal for bandwidth-intensive tasks like streaming high-definition videos.
Additionally, some websites may present CAPTCHA challenges or restrict access to Tor exit nodes, which can be mildly inconvenient for users. It’s advised to keep a standard browser on hand for such situations.
Wrapping Up
In a digital landscape teeming with potential threats to our privacy, Tor Browser stands tall as a guardian of online anonymity. By harnessing the power of a decentralized network and robust encryption, it empowers users to traverse the web without leaving a discernible trace.
However, like any tool, Tor Browser is most effective when used judiciously. Understanding its strengths and limitations is key to maximizing its benefits. So, whether you’re a journalist navigating sensitive sources or an individual seeking to reclaim your online privacy, Tor Browser is a powerful ally in the fight for digital freedom. Embrace it,





